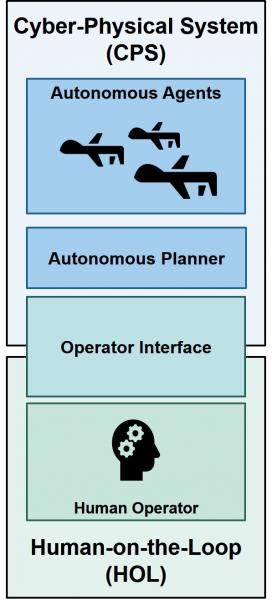
With the advancement and automation involved in cyber-physical systems, human presence is almost inevitable in such systems. The vast majority of applications mandate the presence of a human being with supervisory roles (Human-on-the-Loop), such as goal setting, high-level and moral decisions, and interfering in situations unfamiliar to the autonomous system. Hence, it is vital to understand how this presence affect the performance requirements at design phase. Moreover, this understanding serves a radical change in the design paradigm: can we design autonomous systems that utilize human presence in improving the provided guarantees?
The project is currently focused on exploring the answer to those question for single-operator multi-UAVs command and control systems. Specifically, we examine the human role in security guarantees when UAVs are susceptible to malicious attacks on their GPS sensors. The approach we are following in this project is threefold:
- Understanding human behavior
- Developing representative formal models
- Formally synthesizing optimal protocols
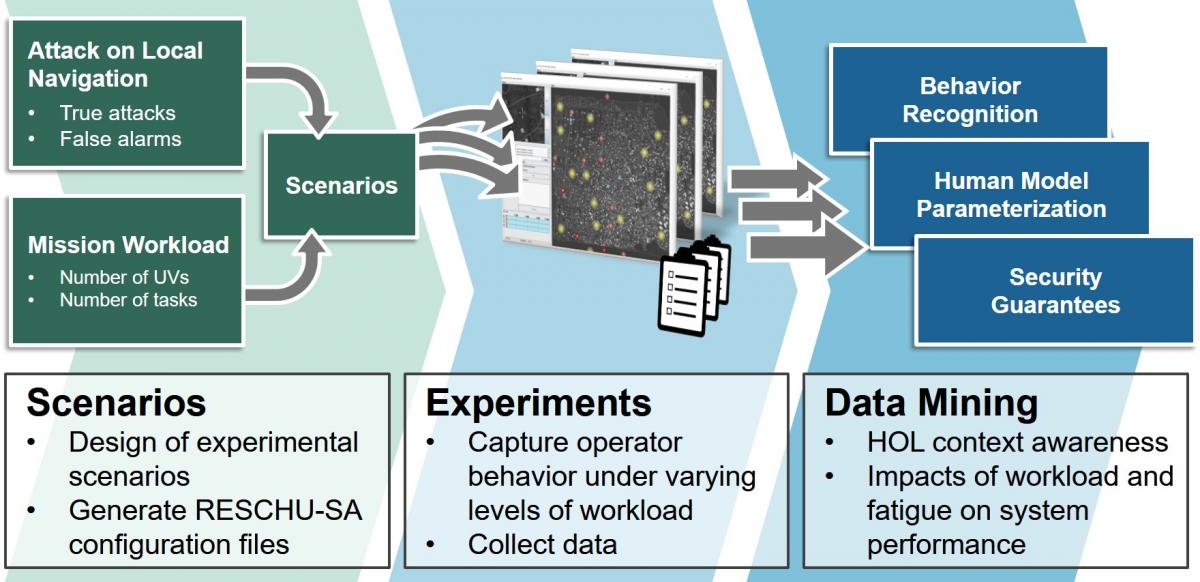
RESCHU-SA Testbed
We developed RESCHU-SA, an extendable virtual platform that facilitates studying the impact that HOL has on the security of CPS with varying levels of autonomy. RESCHU-SA allows users to analyze how the human power of inductive reasoning and ability to provide context, particularly during an attack, affects the overall CPS security guarantees. The proposed platform is an extension of the Research Environment for Supervisory Control of Heterogeneous Unmanned Vehicles (RESCHU) simulation environment, previously used in various applications, including studies focused single- and multi-operator supervision of Unmanned Aerial Vehicles (UAVs) missions, as well as interface usability metrics.
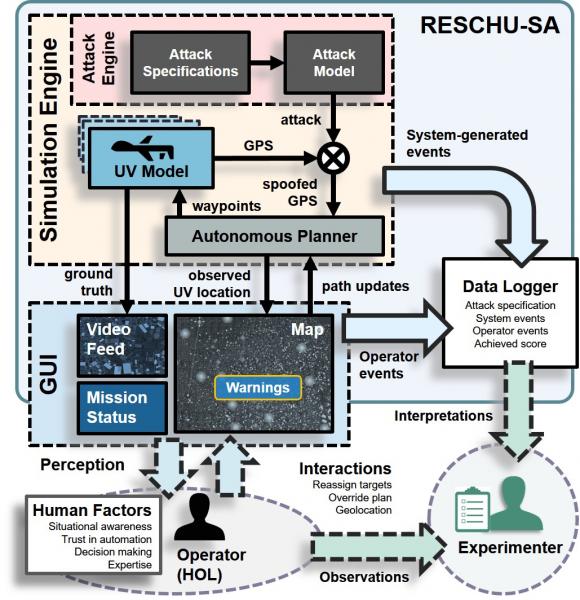
Testbed Features
Feature-Rich Randomized Map. We generate a randomized map with regions of various feature richness. This allows studying how feature density may influence the operator’s adoption of different planning strategies.
Video-Feed Simulation. In contrast to the conventional camera feed that shows a static image of predefined areas on the map, we implement an engine that simulates the video feed received from a UV. The engine allows to access the video feed at any location on the map with the ability to introduce advanced features, such as noise overlay and communication delays.
GPS Cyber-Attack Engine. We allow two modes for each UV. In normal mode, the UV video feed matches its location on the map. In cyber-attack mode, we simulate an adversary injecting malicious GPS coordinates that creates discrepancies between the UV reported location and ground truth as depicted in the map and the video feed, respectively. The engine allows configuring adversary behavior, including aggressive vs. stealthy attacks, timing, target regions, and warnings raised by UVs under attack.
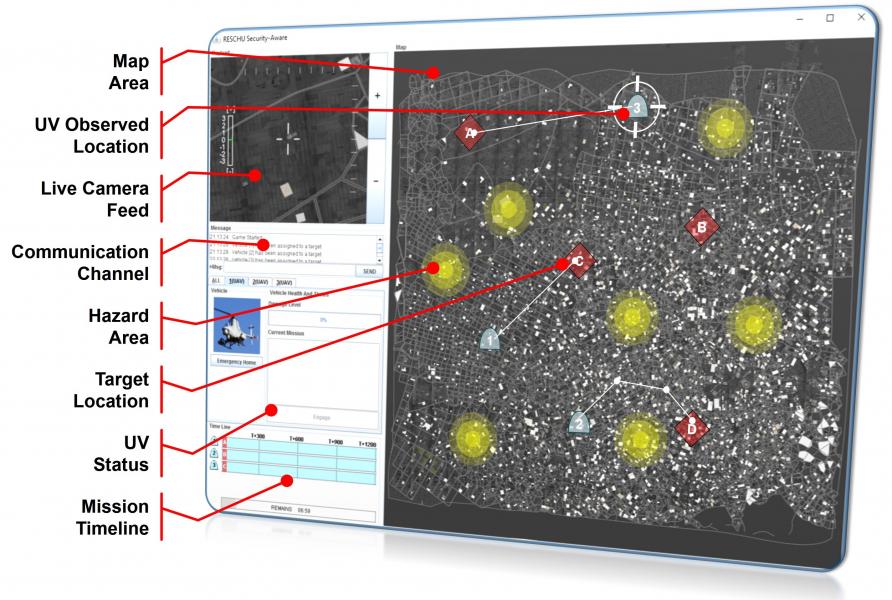
User Interface
Videos
Publications
M. Elfar, Y. Wang, and M. Pajic, "Security-Aware Synthesis using Delayed Action Games", 31st International Conference on Computer-Aided Verification (CAV), 2019
M. Elfar, H. Zhu, M.L. Cummings, and M. Pajic, "Security-Aware Synthesis of Human-UAV Protocols", IEEE International Conference on Robotics and Automation (ICRA), 2019
H. Zhu, M.L. Cummings, M. Elfar, Z. Wang, and M. Pajic, "Operator Strategy Model Development in UAV Hacking Detection", IEEE Transactions on Human-Machine Systems (THMS), 2018
H. Zhu, M. Elfar, M. Pajic, and M. L. Cummings, "Human Augmentation of UAV Cyber-Attack Detection", International Conference on Human-Computer Interaction (HCII), 2018